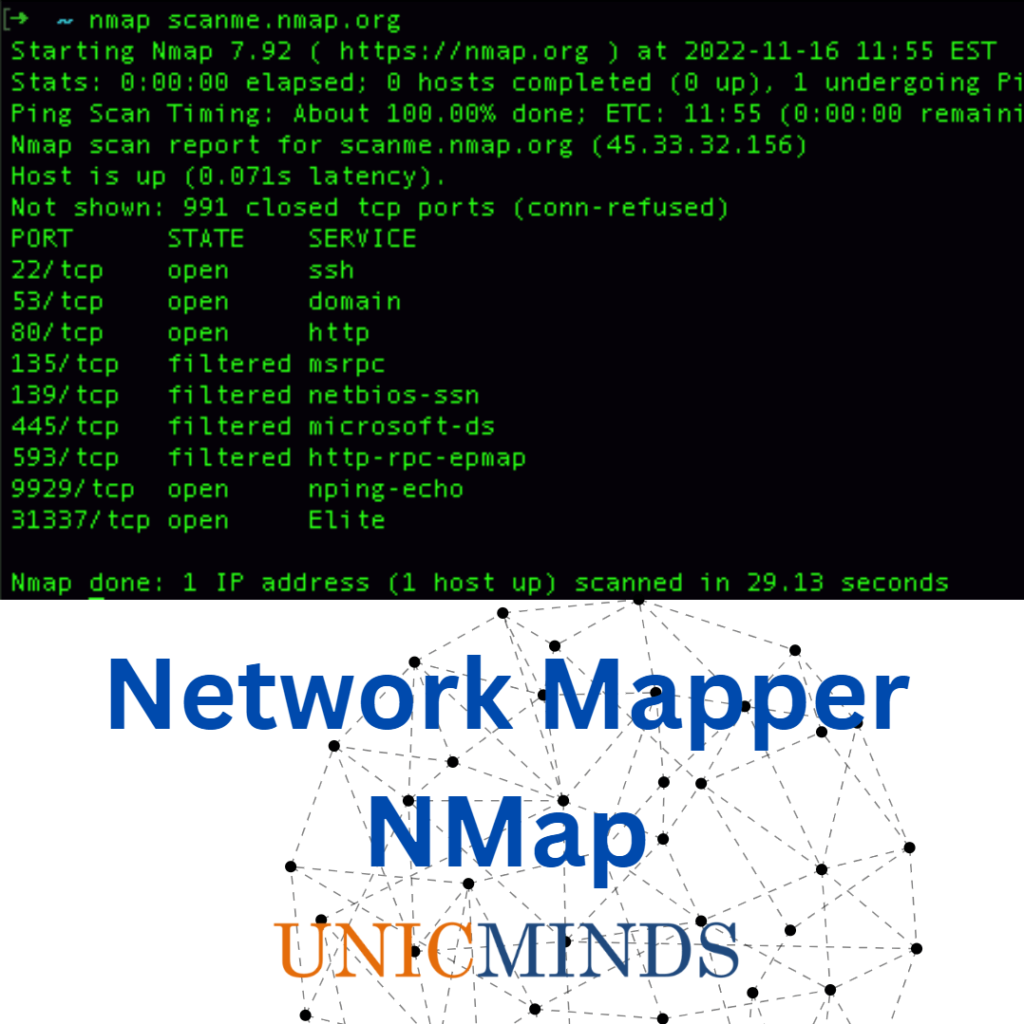
One of the key tools we teach as part of our ethical hacking course is the usage of Nmap. The abbreviation Nmap comes from its usage Network Mapper. Nmap helps us to get real-time information about all IP addresses connected in the network. It gives information about live hosts, open ports and its services, OS of the devices, ping sweeps, and port states. One can say that nmap is like the most important tool-kit of a root or sysadmin or someone who is looking to understand the basics of hacking and network security. Using nmap with other tools such as “ipconfig” and “traceroute” is the ultimate combination to learn the secrets of a network.
Ports are essentially an address or destination within a ‘host’ (computer). When you send data on the Internet, a hostname and port number are specified for where the data should go. The hostname, such as ‘unicminds.com’, is translated into the ‘IP’ address: 160.153.0.147 That identifies the specific computer (NIC) on the Internet. The port number is a 16 bit number (from 0 to 65534) which identifies a service or listener on that computer. For example, port 80 is the usual port for HTTP, for web servers.
You can use nmap to scan your network, find port states, and send packets to understand the real state of a port. But, nmap doesn’t come by default, and hence you need to install it externally. The installation process is easy, but it may vary based on your operating system. Below, we’ve covered how to install an app for Windows, MacBook, and Linux versions.
- For Windows OS: Download and run the custom installer you get with Nmap (namp<version>setup.exe). This will automatically configure Nmap on your Microsoft system.
- For Mac OS: Run the Nmap-<version>mpkg file to start the dedicated installer (you get this with Nmap).
- For Linux OS: Run the following commands after opening the terminal to install Nmap
- $> sudo apt-get install nmap
Running a basic ping scan: only checks which IP addresses are live, doesn’t scan the ports
> nmap -sp 192.168.1.1 (scan a single IP)
>nmap -sp 192.168.1.1 192.168.2.1 (scan specific IP addresses)
You can enter a domain (example.com), an IP address (127.0.0.1), a network (192.168.1.0/24), or a combination of those. Running a Nmap scan may be against the terms of your internet service provider (ISP) and may land you in hot water. Always check and be sure before performing Nmap scans on targets other than your network.
You can use to scan all subnets in one go
>nmap 192.168.1.*
You can use it to scan the OS of hosts in your network. OS scanning is one of the powerful features of Nmap. The way it works is – it sends TCP and UDP packets to the host and checks its response against a very strong database of responses stored in its history.
>nmap -sV IPAddress
Scanning the top ports
>nmap –top-ports n 192.168.1.1.106
Refer to this nmap cheat sheet to understand all the commands you can run using nmap. Essentially, if you want to audit and network and understand the basic information about the various hosts, then you use network mapper to map and understand the network. There is a cousin of nmap called the zenmap (available from nmap.org again) which visually maps your network.
In our ethical hacking course, we cover tools such as nmap, traceroute, netstat, and ipconfig in detail to help the students understand the basics of how network admins and ethical hackers can protect networks against attacks.
Hope this is useful, thank you.
You may like to read: TCP/IP 3 Way Handshake for Client-Server Connection – Explained in Detail, SHA256 Algorithm in Detail, & Binary Trees of Computer Science