Previously, we have seen the different types of ciphers used in communications. These ciphers are used heavily in encryption and hashing. For example, the AES and DES ciphers use many rotations and transpositions. Similarly, we will see the SHA256 hash algorithm in detail using many ciphers that we learnt before.
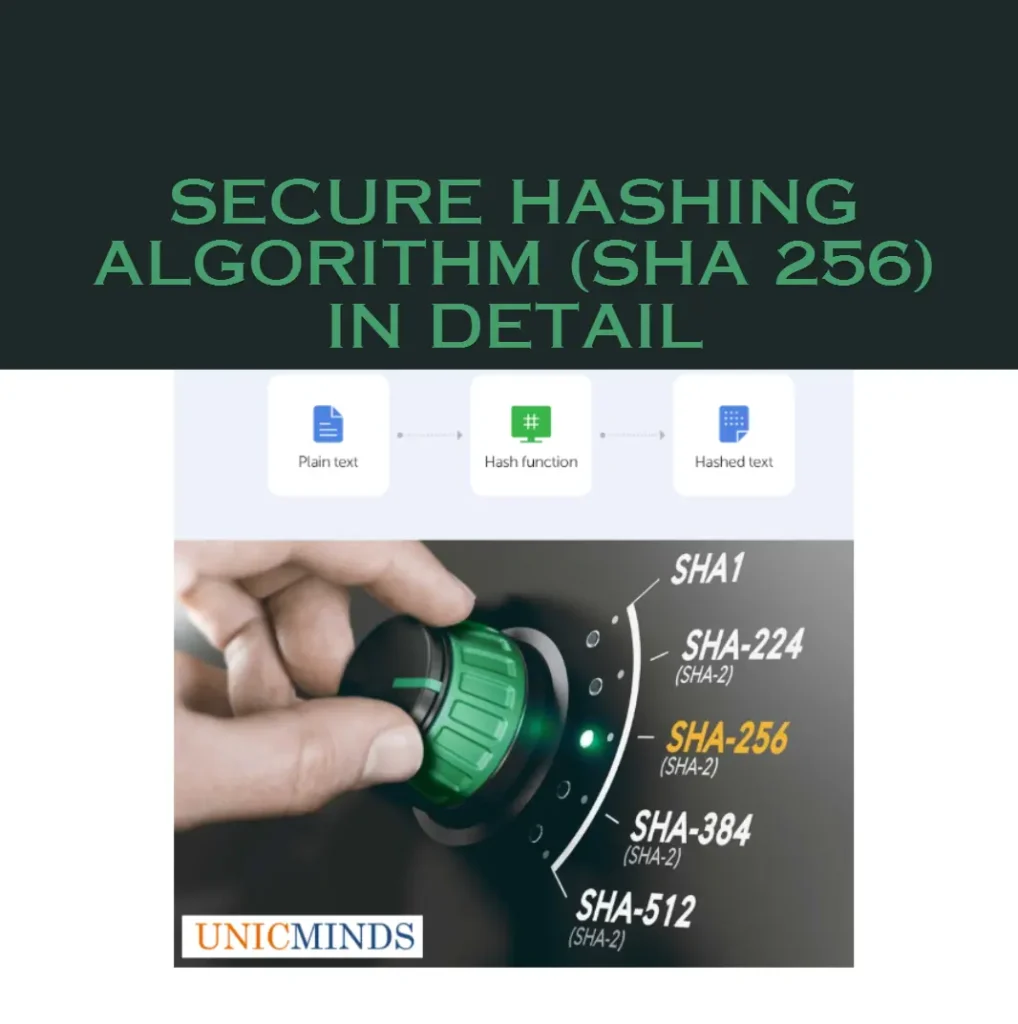
The Secure Hashing Algorithm (SHA) was designed by the National Security Agency, United States. The result that comes out of a hash function is called a Hash Digest. The difference between Encryption and Hashing is that in hashing the hash digest cannot be cracked backwards using mathematical operators except in the case of a Brute-Force attack.
If a single character is changed, then SHA uses the principle of Avalanche Effect and changes the hash digest in a large way. Example: only the first alphabet is changed in the right example.
SHA comes in two forms – SHA 1 and SHA 2. There are other names used such as SHA256, SHA512, SHA384 etc., but these are just variations of SHA 2 with a different bit length. SHA-1 returns a 160 bit hash. SHA-2 can return between 256 to 512 bit hash. SHA-3 is released but is not widely adopted yet. Used in signing digital certificates, SSL/TLS certificates, and hashed password storages, SHA256 is the most popular of all SHA2 algorithm variations.
Steps involved in the SHA-256 Algorithm
- Step 0: You have some data to be hashed… (INPUT)
- Step 1: Convert the data into binary
- Step 2: Pad 0s until you make the length of the message 64 bits less than a multiple of 512.
Maths Operation -> n x 512 = Message + Padding + 64
- Step 3: Add the length of the original message in last 64 bits, making the entire message length to be a multiple of 512 bits
- We now have our message block of n x 512 bits long
- Now, we break the message into 512 bits long (n chunks)
- We do a set of 64 rounds of operations on the first chunk of the data
- So, we have a message chunk of 512 bits, on which we will do 64 rounds of operations.
- Step 5: Create 8 K values
- Step 6: Create chunks of data
- Step 7: We’ll do a set of transpose, right rotations and Right shifts
- Step 8: Create Message Schedule
- Step 9: Compression
- Step 10: Final Hash Value
Hope this is useful, thank you.
You may like to read: TCP/IP 3-Way Handshake in Detail, Making a Program Counter using Multiplexers, & Coding Competitions for Kids