Every computing device, hardware and software, is vulnerable, and at UnicMinds, we teach youngsters all the basics required to understand cyber security and ethical hacking in a comprehensive way including the most updated attacks used in history till date.
Six Different Types of Hackers
In common usage, when we want a person to think about a problem, we say you have to wear the “thinking hat”, with the analogy that the hat you wear represents what is going inside your brain. Using the same analogy, we have 6 different types of hackers. Children will learn about the basics of hashing, encoding, encryption, different types of attacks, malware, protection mechanisms, and more.
Black Hat Hackers – These are criminals hacking without permission and with malicious intent. This is illegal work and when caught these hackers will be tried in court and will be punished with jail-term by the respective law of the land.
White Hat Hackers – These are security professionals who take permission and find vulnerabilities in systems. They also help close the security vulnerabilities. Many times, black hat hackers convert to become white hat hackers for various companies.
Grey Hat Hackers – These are somewhat between white and black hat people. Grey hat hackers don’t harm the systems but at the same time they don’t take permission to attack too. They are doing it for learning, sport, and fun, and don’t mean harm.
Green Hat Hackers – These are the beginners in hacking, learning from the basics and smaller system attacks.
Blue Hat Hackers – These are professionals hired by software companies to find loopholes and vulnerabilities in their software products. For example, to ensure there are no supply-chain attacks or side-channel attacks or direct vulnerabilities, many companies hire these hackers.
Red Hat Hackers – These are the ones who stop the black hat hackers from attacking government and critical infrastructure such as military, defence, telecom, and others. These hackers are hired by governments for their own goals and defence.
Learning Ethical Hacking and Cyber Security at UnicMinds
At UnicMinds, the ethical hacking and cybersecurity course is one of the most exhaustive courses starting from the basics of IP addresses and networking basics to Kali Linux tools, SQL injections, and antivirus software.
Detailed Summary of Ethical Hacking Curriculum:
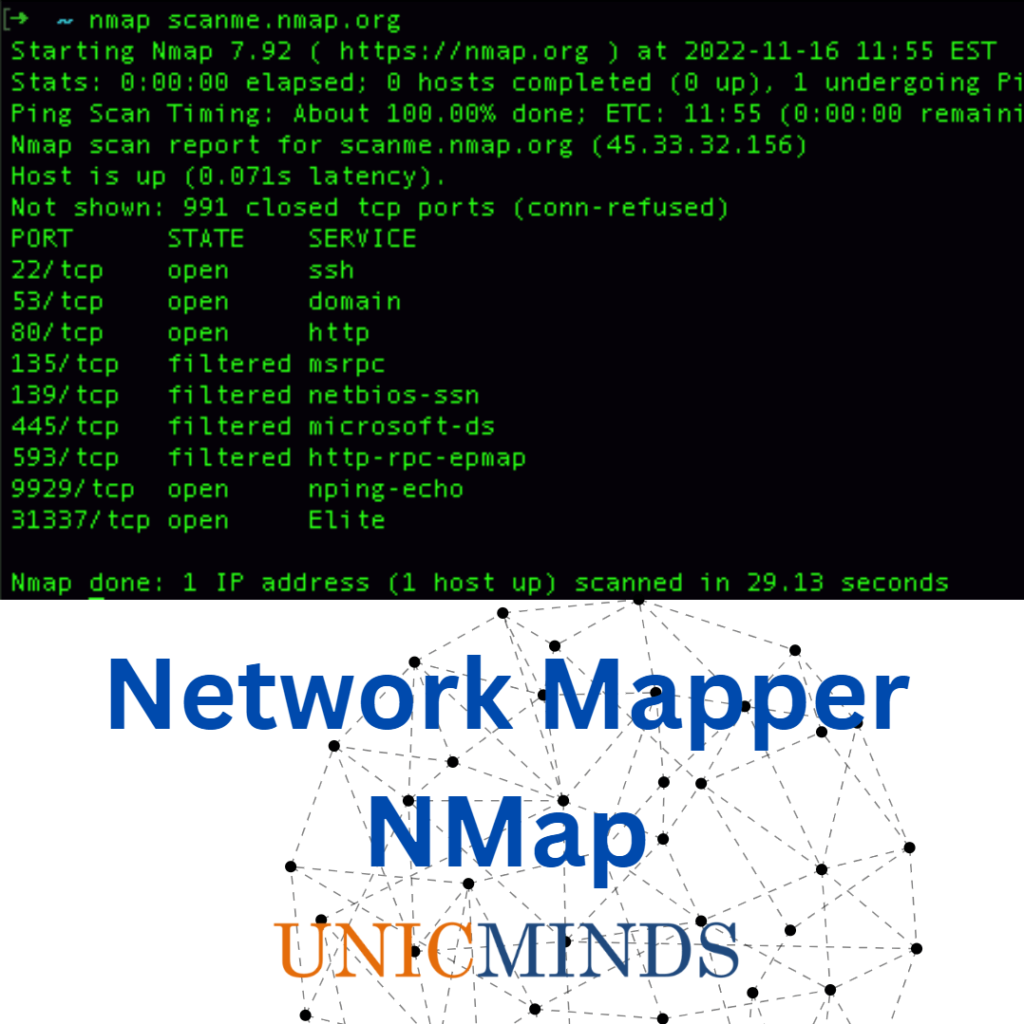
- Introducing ipconfig, ping, nslookup, dig, host, traceroute, and netstat commands.
- Overview of Internet Architecture
- Basics of Computer Networks
- What is a Protocol?
- Basics of TCP/IP
- Ethical Hacking Orientation
- Introduction to Windows vs. Linux
- Different types of Users and Permissions in Operating System
- Theory on types of attacks on Android and iOS phones
- Theory on IP, Host, LAN, WAN, Router and Firewall
- Theory of Malware, Spyware, Sniffing, and Denial of Service attacks
- Theoretical basis of Keylogger Algorithms
- Basics of Cryptography and good password practices
- Public Key Encryption Methods
- Intro to Kali Linux and File Structure
- Basic hacking techniques used in Kali Linux
- Da Vinci and ancient cryptography
- Hash vs. Encryption vs. Encoding
- Various Types of Ciphers
- Writing small encryption algorithms
- Penetration Testing with permission
- Web Cookie Analysis, SQL Injection Basics, & Cross-site Scripting Basics
- RLO naming for Trojans
- Electro-magnetic Spectrum, Radio Waves, nRF module, & Faraday Cages
- Vulnerabilities of Connected Devices & Juice Jacking
- Approach of Self-Replicating Programs (Quines)
- Intrusion Detection Systems, Process Hollowing, & Anti-virus Software
- Boot Sector, Polymorphic, Multipartite, Macro, and other viruses
- Hardware Trojans & Side-Channel Attacks
- Google Dorking
- CyberLaw, Cyber Regulations, & Digital Forensics
- Good and Safe Internet Practices for Kids
- Recap Lessons on Ethical vs. Unethical Hacking
- Writing simple reports
Tools such as Kali Linux, OWASP ZAP, bWAPP, Metasploitable, Google Gruyere, PentesterLab, and WebGoat. Students will understand all the various types of malware, spyware, trojans, quines, and different types of attacks. Students will also learn extensively about the law and regulating bodies around cybersecurity in India and the US.
With AI & ML becoming more and more prevalent, the future of hacking will be in the cloak of machine learning systems and tampering with the models within ML systems. Ethical Hackers are expected to be in high demand in the next five years with high average salaries. Ethical Hackers help the infrastructure around us be safe to use and are an incredibly important part of our societies.
If you want to book a free ethical hacking trial class, click here.
Learn more about Ethical Hacking & Cyber Security for Juniors, SSL Certificate, HTTPS, & TCP Handshake Basics, and how are Prime Numbers and Encryption related.