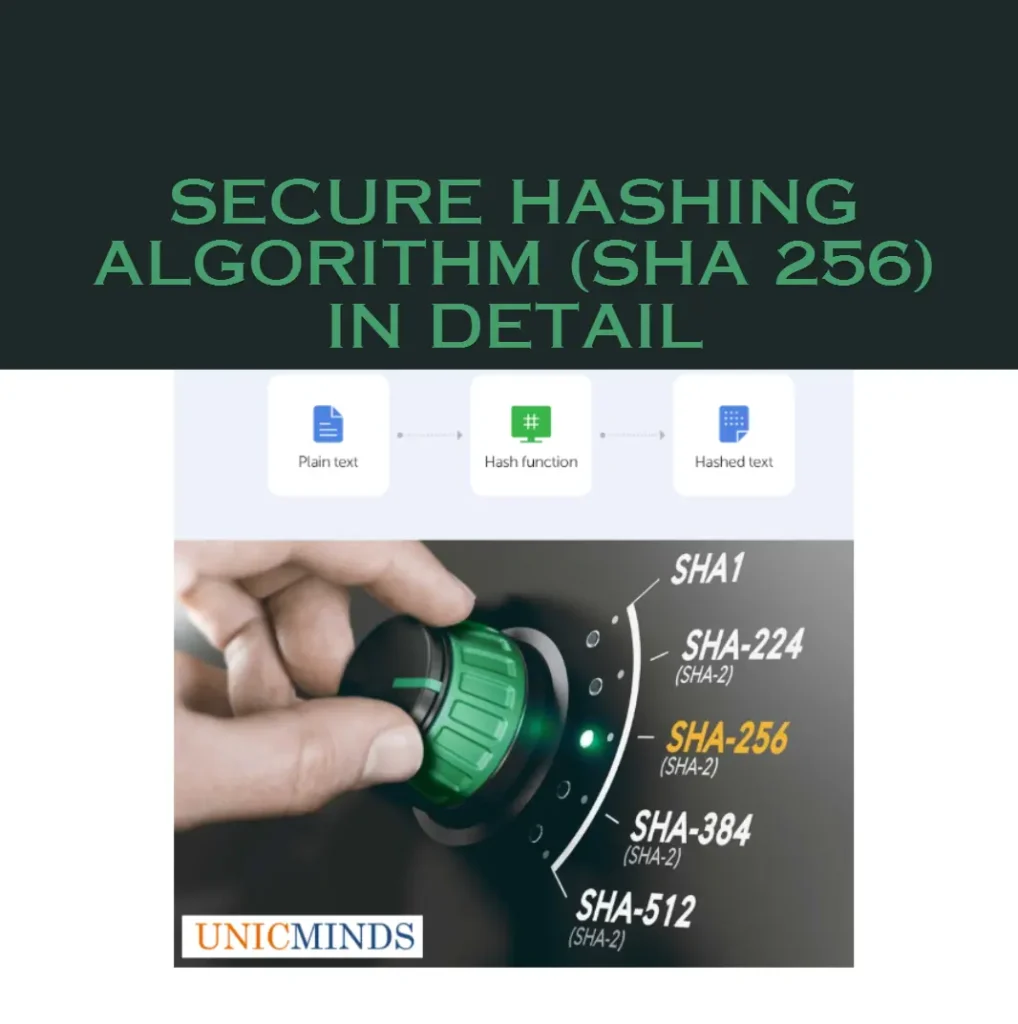
Secure Hashing Algorithm (SHA256) in Detail
Previously, we have seen the different types of ciphers used in communications. These ciphers are used heavily in encryption and hashing. For example, the AES and DES ciphers use many rotations and transpositions. Similarly, we will see the SHA256 hash algorithm in detail using many ciphers that we learnt before. The Secure Hashing Algorithm (SHA) […]
Secure Hashing Algorithm (SHA256) in Detail Read More »