Below are the three steps to decrypt 802.11 wireless traffic in Wireshark.
- Go to Edit -> Preferences -> Protocols -> IEEE 802.11.
- Click on the “Edit…” button next to “Decryption Keys” to add keys.
- Check the decrypted wireless traffic
But wait, it is not that simple. These steps are used after you capture the data from an access point and to decrypt that particular data. But, to get access to the data from an access point, we need to establish a four landmark handshake between the client and the access point. But, what are clients and access points?
Client vs. Access Point
In networking, a client is a device that requests information from a server or an access point. An Access Point (AP) is usually the name used to refer to a device that provides WiFi service to a particular area in Managed mode. It is called AP and the client connecting is called STA (short form for station). Please note that a networking device can operate in STA mode or AP mode depending on whether it is a device acting as a client or it is a device acting as a hub of a wireless network (allowing other devices to connect to it).
What exactly happens when a client connects to a WiFi network
Pre-Shared Key (PSK):
When you connect to a WiFi network, the PSK (your WiFi password) is used as a “seed” to generate a shared secret key between your device and the access point.
Diffie-Hellman Key Exchange:
The device and router use the Diffie-Hellman protocol to establish this shared secret key, which is not transmitted in plain text.
Encryption and Decryption:
Once the shared key is established, it’s used to encrypt and decrypt the data transmitted between your device and the access point.
Wireshark:
To passively decrypt WiFi traffic, tools like Wireshark can be used, but you’ll need to know the PSK and capture the 4-way handshake that occurs during the connection to the access point.
WPA3:
In WPA3, a different PMK is used for each connection. Capturing the handshake and knowing the network password alone isn’t sufficient; you’ll need the PMK (either from the client or access point) to decrypt packets.
So, to decrypt WiFi traffic is needed:
- a handshake that occurred between the Client and the Access Point immediately prior to the exchange of decrypted information
- for this we need Monitor Mode WiFi adapter
- password to connect to the Access Point
Next will be shown two examples of capturing WiFi traffic and its decryption. The first data capture is performed using Airodump-ng , and then the wireless traffic will be decrypted in Wireshark. In the second example, the data will be captured and decrypted using only Wireshark .
Capture WiFi traffic using Airodump-ng
In order for the data to be suitable for decryption, it is necessary that the WiFi card does not switch channels, but to capture information on one channel on which the target Access Point operates. Therefore, we start by collecting information about the target access point.
We look at the names of wireless interfaces:
| iw dev |
We translate the INTERFACE into the monitor mode with commands like this:
| sudo ip link set INTERFACE downsudo iw INTERFACE set monitor controlsudo ip link set INTERFACE up |
Change INTERFACE with your WiFi adapter name
Run airodump-ng with a command like:
| sudo airodump-ng wlan0mon |
For example, I want to capture and decrypt traffic for the Kali Access Point, which operates on channel 5.
Then I need to restart airodump-ng with a command like this:
| sudo airodump-ng wlan0mon –channel CHANNEL –write FILE NAME |
The WPA handshake inscription says that a four-stage handshake was captured. It means that:
- Now we can decrypt the WiFi data (if we have the key to the WiFi network)
- we can only decrypt data for a specific client (with which a handshake was made)
- we will be able to decrypt the data that was sent only after this captured handshake
Decryption of WiFi traffic using Wireshark
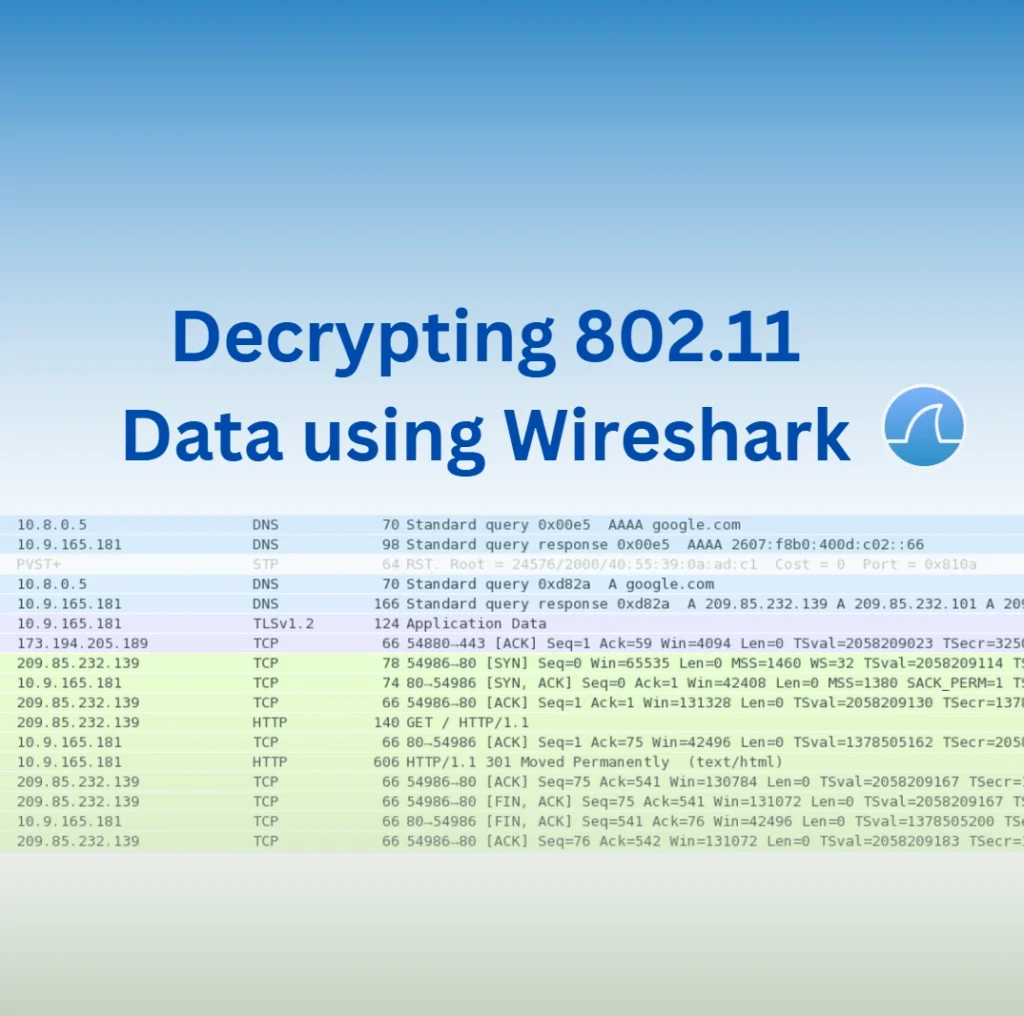
Open the capture file in Wireshark. In its original form, traffic looks like this:
That is, without decryption, we see only the MAC addresses of the data transfer participants, some types of packets, as well as data packets — in which the payload is encrypted.Before decoding, make sure that there is a handshake, otherwise there is no point in continuing:
| eapol |
Before decoding, we need to make some changes in the IEEE 802.11 protocol settings.
Go to Edit → Preferences , expand the protocol section and select IEEE 802.11 . The settings should be:
make sure you have the same settings as in the previous screenshot, click on the Edit button next to Decryption Keys (to add a WEP / WPA key):
Click the Create button . In the window that opens, in the Key type field, select wpa-pwd , enter the password for the WiFi network, and after the colon, enter the network name (SSID) and click OK.
For example, in my case, the password is qivxy17988, and the network name is Kali, then I enter:
| qivxy17988:Kali |
Click Apply :
Traffic will be decrypted:
Now there are visible DNS, HTTP requests and responses, as well as other network packets.
If traffic is captured not only for this network, but also for other networks operating on the same channel, or for this network but other clients for which no handshakes are taken, then this traffic will not be decrypted.
Capture wifi traffic with wireshark
WiFi traffic can be captured directly in Wireshark.
But we first need to switch the WiFi card to the same channel as the target Access Point. This is done by commands like:
| sudo ip link set INTERFACE downsudo iw INTERFACE set monitor controlsudo ip link set INTERFACE upsudo iw dev INTERFACE set channel |
The subsequent decryption is performed in exactly the same way as shown above.
Conclusion
To decrypt WEP WiFi traffic, you only need to know the password.
You may like to read: Monitor and Injection modes in Wireless Adapters, Structures in C Programming, & Is quantum computing a threat to encryption?
Source(s):